-
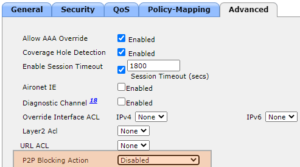
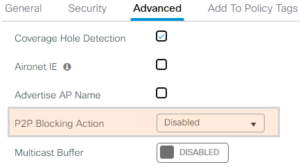
What is Peer-2-Peer blocking?
Peer-2-peer (P2P) blocking is a security feature allowing an administrator to drop (or force to switch upstream) data traffic between clients associated to the same WLAN. P2P is mostly deployed in Guest WLANs where you don’t want your clients to be able to communicate between each others.
This settings can be modified on the Advanced Settings of the WLAN (for AireOS & IOS-XE) WLC
-
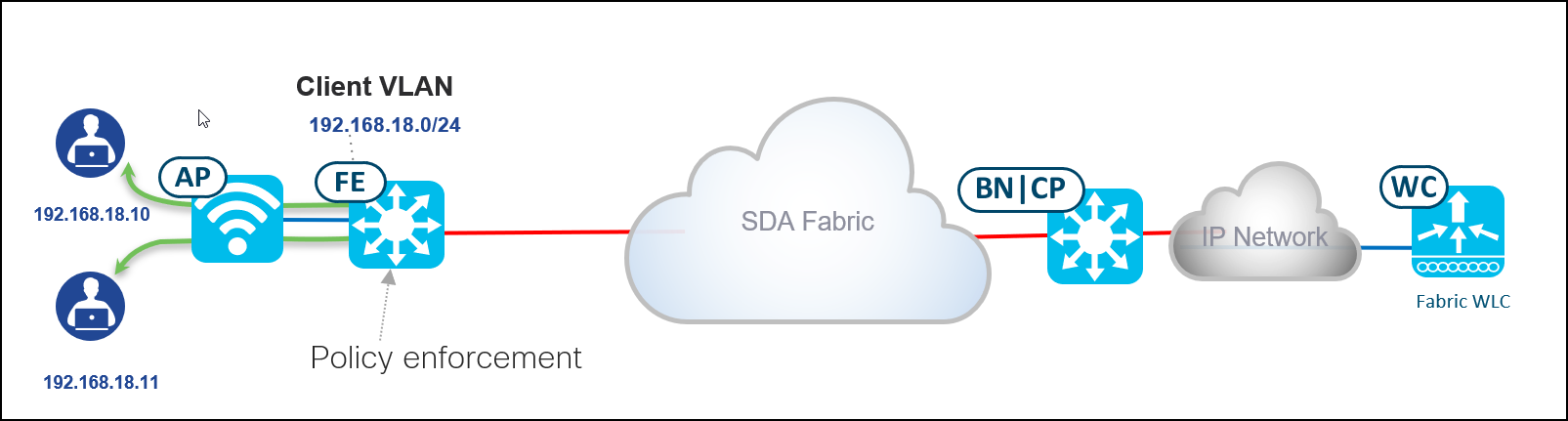
What is the impact of enabling SDA for Wireless?
When extending SDA to Wireless world, traffic between two clients connected to the same WLAN and same AP will always be switched at the Fabric Edge level. Basically, the Access Point will encapsulate data traffic into VxLAN tunnel between Access Points and Fabric Edge, in order to make sure that policy enforcement (TrustSec) is applied to the traffic.
Therefore, P2P policy enforcement at the AP level is no longer working : Access Point is sending all traffic upstream. In order to block communication between peers on the same WLAN & same AP, you have to leverage Cisco Trustsec Policy and SGACL. Configuration steps is detailed below.
-
Peer-to-Peer blocking with TrusSec Config (DNAC 2.2.3.4)
- Configure your TrustSec policy as you would do for micro-segmentation in your wired network : Policy > Group-Based Access Control > Policies– In the below example, PC to PC communication is mapped to the contract named “Deny ip” which is the default one to deny all traffic.
If you need more granularity, you can configure specific contracts and assign it to matrix.
- Configure your TrustSec policy as you would do for micro-segmentation in your wired network : Policy > Group-Based Access Control > Policies– In the below example, PC to PC communication is mapped to the contract named “Deny ip” which is the default one to deny all traffic.

-
- Click Deploy to push this config to ISE. Once done, if you have at lease one wireless client with SGT “PC” you should see the SGACL in your WLC. On IOS-XE you can browse Configuration > Security > TrustSec > CTS Policies, or through CLI with the command show cts policy sgt
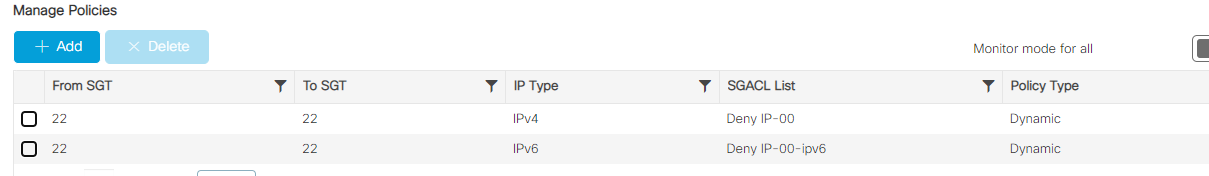
- Click Deploy to push this config to ISE. Once done, if you have at lease one wireless client with SGT “PC” you should see the SGACL in your WLC. On IOS-XE you can browse Configuration > Security > TrustSec > CTS Policies, or through CLI with the command show cts policy sgt
-
Caveats
- If you perform this configuration while affected users are connected, you may have to shutdown the WLAN in order to reset the session and apply the SGACL
- If your WLAN is mapped to a Fabric-Enabled Policy Profile as well as a Non-Fabric-Enabled Policy Profile, you still need to define the P2P blocking action for non-SDA Access Points.
Reference:
https://www.cisco.com/c/en/us/td/docs/solutions/CVD/Campus/cisco-sda-design-guide.html
Thanks for this informational blog. If possible please make more blog post on Wireless or ISE integration with SDA.