In this post, we will see how to configure an IOS autonomous access point to act as 802.1X supplicant.
For the setup, I have a :
- 3502i AP – 15.3(3)JD16 (8.3.143.0)
- 3750G switch – 12.2(55)SE9
- ISE appliance 2.2
-
ISE Configuration
- Add the AP as Network Devices : Administration > Network Resources > Network Devices > Add. You can also create a Endpoint Identity Groups to help the selection of Policy Sets.
- Create an Authentication Allowed Protocol list : Policy > Policy Elements > Authentication > Allowed Protocols. For this setup, I decided to use EAP-FAST
- Create a Identity Group on which you will create a new user:
- Administration > Identity Management > Groups > User Identity Groups > Add
- Administration > Identity Management > Identities > Users > Add. Don’t forget to add it to the newly Id Group
- Create the policy set. As you can see below, the one I created is really light but conditions and authorization profiles can be modified as wished.
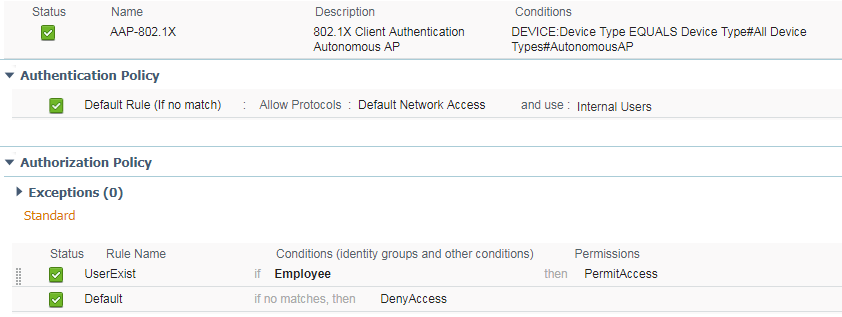
-
AP Configuration
The configuration is pasted below with some comments :
#Create a new EAP Profile with the chosen EAP methods eap profile PROFILE-FAST method fast #Configure the credentials to be used for EAP-FAST authentication dot1x credentials EAP-SUP username ap1234 password Test1234 #Configure the wired interface to authenticate using the credentials and EAP profile configured interface GigabitEthernet0 dot1x pae supplicant dot1x credentials EAP-SUP dot1x supplicant eap profile PROFILE-FAST
-
Switch Configuration
#Enable AAA and use RADIUS group for 802.1X authentication aaa new-model aaa authentication dot1x default group radius #Enable 802.1X globally dot1x system-auth-control #Configure the interface to authenticate supplicant with 802.1X interface GigabitEthernet1/0/11 description Light AP - WLC02 switchport access vlan 30 switchport mode access authentication port-control auto authentication host-mode multi-host dot1x pae authenticator #Configure the RADIUS server radius-server host 172.16.10.14 auth-port 1812 acct-port 1813 key cisco
-
Verification/Troubleshoot
From the switch side, as soon as the AP is authenticated, you should see this kind of message in the logging :
%AUTHMGR-5-SUCCESS: Authorization succeeded for client (c89c.1d0d.ad3f) on Interface Gi1/0/11 AuditSessionID AC100A010000000A00614C98
You can verify the authentication status using this command : show authentication sessions interface <if-name>
Switch#sh authentication sessions int gi1/0/11 Interface: GigabitEthernet1/0/11 MAC Address: c89c.1d0d.ad3f IP Address: Unknown User-Name: ap1234 Status: Authz Success Domain: DATA Security Policy: Should Secure Security Status: Unsecure Oper host mode: single-host Oper control dir: both Authorized By: Authentication Server Vlan Group: N/A Session timeout: N/A Idle timeout: N/A Common Session ID: AC100A010000000A00614C98 Acct Session ID: 0x0000000C Handle: 0x4A00000A Runnable methods list: Method State dot1x Authc Success
On ISE side, you can review the RADIUS live logs and log details : Operations > RADIUS > Live Logs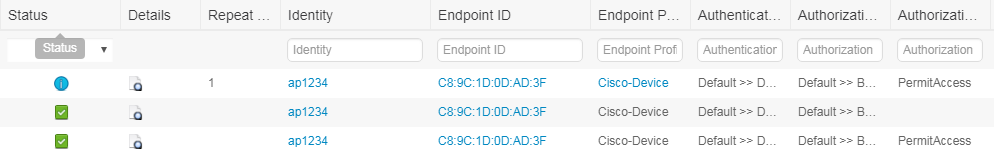
The details should be smilar to the one below :
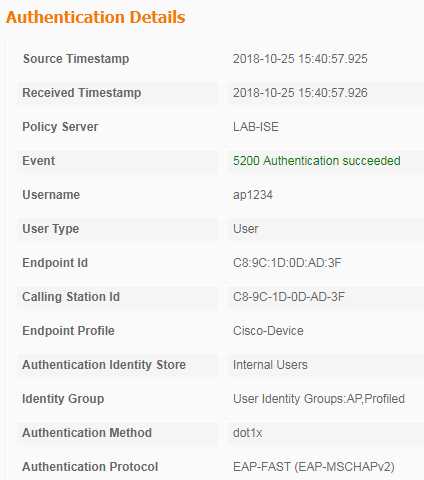
On the AP itself, you can validate the credentials and EAP profile in use :
AAP02#show dot1x interface gigabitEthernet 0 Dot1x Info for GigabitEthernet0 ----------------------------------- PAE = SUPPLICANT StartPeriod = 30 AuthPeriod = 30 HeldPeriod = 60 MaxStart = 3 Credentials profile = EAP-SUP EAP profile = PROFILE-FAST
Do not hesitate to fine-tune the settings (Authorization profile, Conditions, Switch config, …) as it’s a very basic configuration.
Feel free to ask questions if you have any.