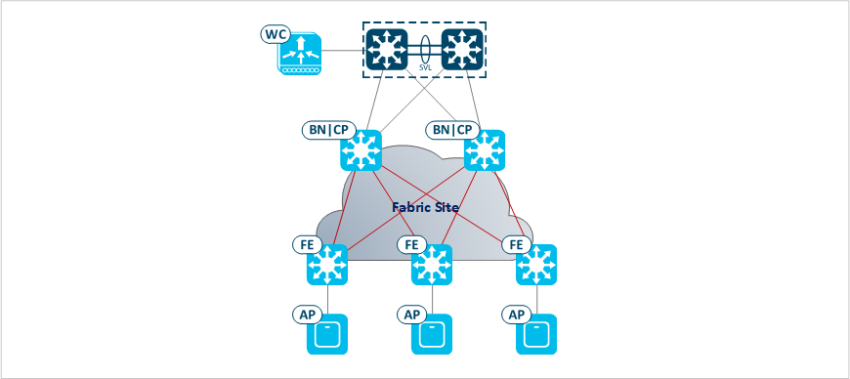
Web Sequence Diagram
The Web Sequence Diagram below show the step-by-step process to get Access Point in “SDA mode”. Steps are detailed below.
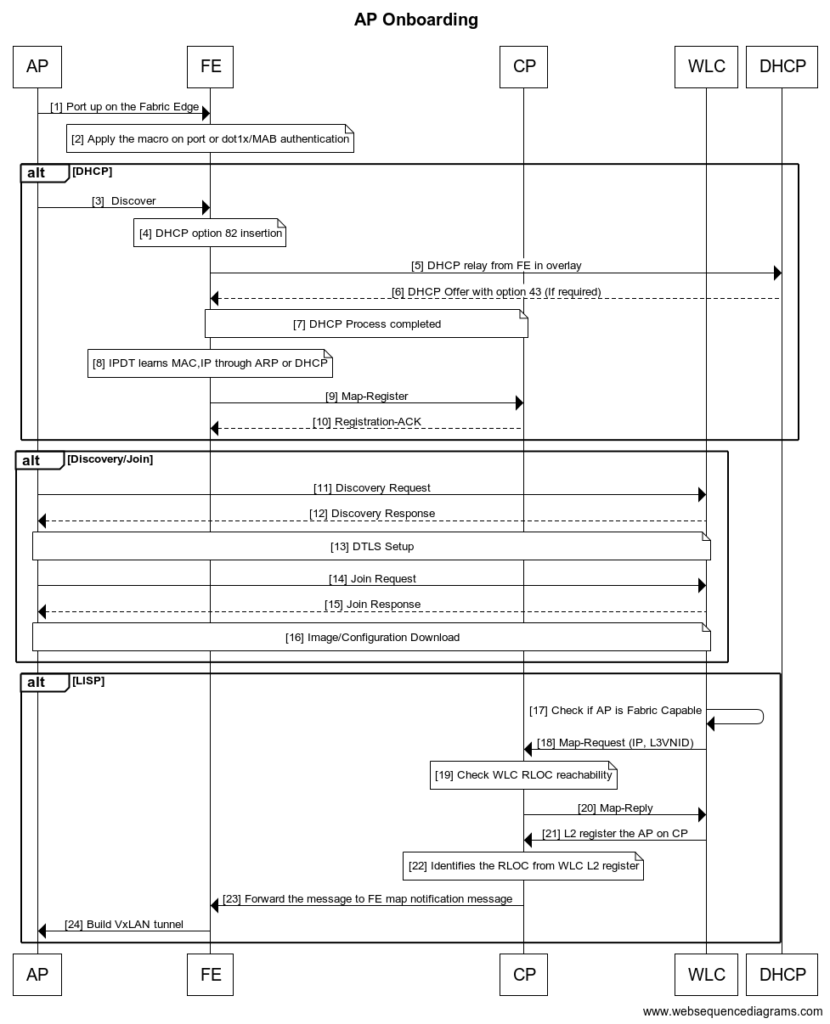
Detailed Step-by-Step Process
- AP is powered through PoE/Power-brick or Power Injector and switchport is going to Up/Up state as the AP boot up;
- At this step, two options are available based on the configured Authentication Template in DNAC :
- Open Authentication – Fabric Edge (FE) will apply a macro on the switchport as soon as it gets CDP information from the AP, providing the Vlan ID for the AP to be part of the underlay network
- Closed Authentication – MAB/dot1x authentication will happen and the result will define the switchport configuration. DNAC automates a template on FE name “ApAutzTemplate” which can be returned as RADIUS attribute by AAA Server. NOTE: By default Access Points are not configured to perform 802.1X as supplicant, so we may need to enable Profiling on ISE for, at least, the first authentication.
- Once boot is completed, first process is DHCP to get an IP address;
- This DHCP Discover is treated by DHCP Snooping at the FE level and the FE will append suboptions (150, 151 and 152) in option 82 in order to add its RLOC (Loopback IP) as the Remote ID. It also sets the giadress as the Anycast SVI address;
- DHCP messages are exchanged at the overlay level to the DHCP server (Configured on DNAC). It can be exchanged at the underlay level in some specific case;
- Option 43 can be added on the DHCP Scope as part of the CAPWAP Discovery process;
- Once DHCP Ack is received by the DHCP Server, IP is installed on the AP;
- At the same moment, IPDT learns MAC & IP address through DHCP Snooping. It can also get this information via ARP Request or GARP;
- As any endpoint connecting to FE, Map-Register is sent to Control Plane (CP);
- CP reply with a Registration-ACK message;
- Discovery request is/are sent to one or multiple WLC(s) based on the method available (DHCP, DNS, L3);
- Discovery Response is received by the AP with some information such as WLC Name, AP-Manager IP, WLC Utilization, Time Sync, …;
- DTLS Tunnel is made up (Cert exchange and so on). Once done, next CAPWAP-Control messages will be encrypted;
- Join request is sent by the AP with few elements (Local IPv4/IPv6, Transport Protocol, …);
- Join Response is send by the WLC with among other things : Result code and image identifier. Image identifier will help to know if Image Upgrade is required or not;
- Image Upgrade and/or Configuration is performed at this step. If upgrade happens, AP will reload and start again the process;
- Once the AP is in Run state, WLC will check if it’s Fabric Capable based on model and software;
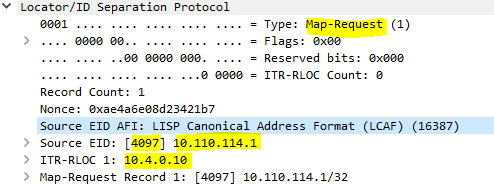
- If AP is not SDA Capable, process stops. If AP is SDA Capable, Map-Request is sent to CP;
May 27 13:09:26.822: LISP[TRNSP]-0: Processing received Map-Request(1) message on Vlan3001 from 10.110.114.1:4342 to 10.110.114.1:4342.
May 27 13:09:26.822: LISP[MR ]-0: Received Map-Request with 1 records, first EID IID 4097 10.110.114.1/32, source EID 10.110.114.1, nonce 0xAE4A6E08-0xD23421B7.
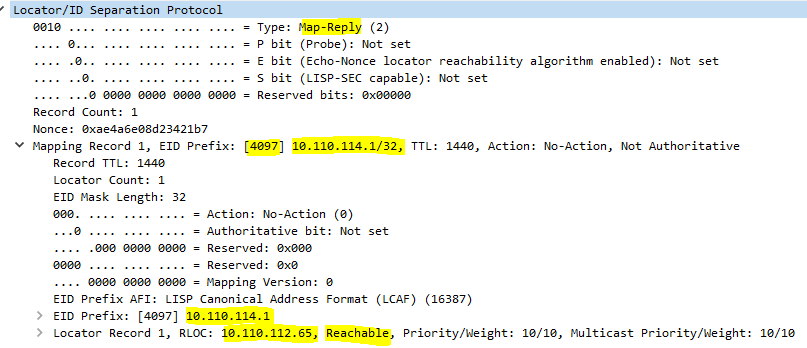
- At the same time, CP check reachability state with WLC, CP is required to have a specific route to WLC (in underlay) to pass this check;
- Map-Reply is sent to the WLC with reachability information;
May 27 13:09:26.823: LISP[MR ]-0 IID 4097 IPv4: MS EID 10.110.114.1/32: Sending proxy reply to 10.4.0.10.
- WLC send a “dummy” Map-Register with L2 information (L2VNID) and A-bit set so CP understand it’s an AP and not a client;
May 27 13:09:26.825: LISP[MS ]-0: Processing WLC Map-Register for AP.
May 27 13:09:26.825: LISP[MS ]-0: Received Map-Register mapping record for IID 8191 MAC 70b3.1786.0420/48 LCAF 2, ttl 1440, action none, authoritative, 1 locator.
May 27 13:09:26.825: LISP[MS ]-0: 10.110.112.65 pri/wei/dID/mID/met=0/0/0/0/4294967295 LpR.
May 27 13:09:26.825: LISP[MS ]-0 IID 8191 MAC: MS EID 70b3.1786.0420/48: Created.
May 27 13:09:26.825: LISP[MS ]-0 IID 8191 MAC: MS Site EID 70b3.1786.0420/48 site 'site_uci': Created dynamic site EID prefix entry.
May 27 13:09:26.825: LISP[MS ]-0: Session 10.4.0.10 port 4342: Received reliable message 'wlc registration' for IID 8191 EID 70b3.1786.0420/48.
May 27 13:09:26.825: LISP[MS ]-0 IID 8191 MAC: MS rr client 10.4.0.10: Created.
May 27 13:09:26.825: LISP[TRNSP]-0: Session User 'reliable-registration-ms' 10.4.0.10 port 4342: Init.
May 27 13:09:26.825: LISP[MS ]-0 IID 8191 MAC: Registration 70b3.1786.0420/48: Created in site 'site_uci'.
May 27 13:09:26.825: LISP[MS ]-0 IID 8191 MAC: Registration 70b3.1786.0420/48: Processing WLC [de]registration.
May 27 13:09:26.825: LISP[MS ]-0 IID 8191 MAC: MS EID 70b3.1786.0420/48: Scheduling WLC mapping notifications to old RLOCs.
May 27 13:09:26.825: LISP[MS ]-0 IID 8191 MAC: Registration 70b3.1786.0420/48: Adding locator 10.110.112.65.
- CP identifies the RLOC from the Map-Register and forward this information to the FE with a Map-Notify message (Step 23);
May 27 13:09:26.826: LISP[MS ]-0: Building reliable message 'WLC Map-Notify' for IID 8191 EID 70b3.1786.0420.
May 27 13:09:26.826: LISP[MS ]-0 IID 8191 MAC: MS EID 70b3.1786.0420/48: WLC Map-Notify has 1 MAC, 0 host IP and 22 bytes of WLC opaque data and 0 bytes of reg opaque data.
- VxLAN Tunnel is built between Fabric Edge and Access Point. Remember that client traffic will go through this tunnel to have policies applied at the FE level.
Go further
In order to go further, I really encourage you to check the following ressources :
RFC 6830 – The Locator/ID Separation Protocol (LISP)